HSTS policy with ASP.Net Core 2.1
One of the novelties of ASP.NET Core 2.1 is that it automatically redirects all traffic from HTTP to https and, in addition, forces the use of HSTS. I am sure you know HTTPS well enough, we rather see how to use HSTS policy with ASP.Net Core 2.1
What is HSTS?
HSTS is simply is a web security policy mechanism by which the server informs the user-agents that it only accepts secure connections, that is, they must use HTTPS to access their resources. Although HSTS has its limitations (and to avoid them, a protocol at the DNS level and not servers) is necessary, its use is an essential practice in web security. In fact today there is NO EXCUSE FOR NOT USING HTTPS NOR HSTS in any website. It does not matter what it does. Not using https or HSTS is a negligence that should embarrass anyone.
ASP.NET Core and HSTS
So far in ASP.NET Core 2.0 we did not have a “built-in” way to force the use of HTTPS or HSTS, although it was not something complex to achieve either. But it is good that they have incorporated it into the framework: now we have a canonical way of doing it. The default template of VS (and dotnet create ) creates the following code in the Configure method:
if (env.IsDevelopment())
{
app.UseDeveloperExceptionPage();
}
else
{
app.UseHsts();
}
app.UseHttpsRedirection();
We have two new middlewares :
- UseHsts : Enables the use of HSTS, which basically consists of sending a header
- UseHttpsRedirection : This is the middleware that converts all HTTP addresses to 301 with HTTPS
Of course, when we launch an application that requires https, we enter the fascinating world of TLS certificates: we need a certificate for the browser to accept loading the page and this certificate must be signed by a recognized certification authority (CA). The first time you are going to run from VS you will receive the following message:
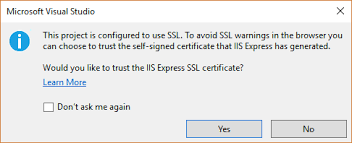
If you click “Yes” then that: it will install a development certificate for the browser to accept loading the data.
If you hit “No” then it does not install it and your browser will return an ERR_CERT_AUTHORITY_INVALID and you will get the typical “unsafe site” error page.
If instead of VS you use the command line when making a “dotnet run” nothing special will happen, but if you access the application, you will receive the same certificate error despite having installed it before. The reason is that the certificate you installed when using VS is that of IIS Express, not that of Kestrel. Remember that an ASP.NET Core application can be run from IIS Express or from Kestrel. To install the Kestrel certificate you must use the following command:
dotnet dev-certs https --trust
From now on you can navigate using https without any issue.
I would highly suggest using HSTS policy with ASP.Net Core 2.1 wherever possible in your web application.
There is also a very good article about HSTS here.